nextcloud-talk-high-performance-backend
This is an old revision of the document!
Table of Contents
Nextcloud - janus, signaling, coturn
Software:
- Janus Gateway (
apt install janus) - Coturn (
apt install coturn)
Settings
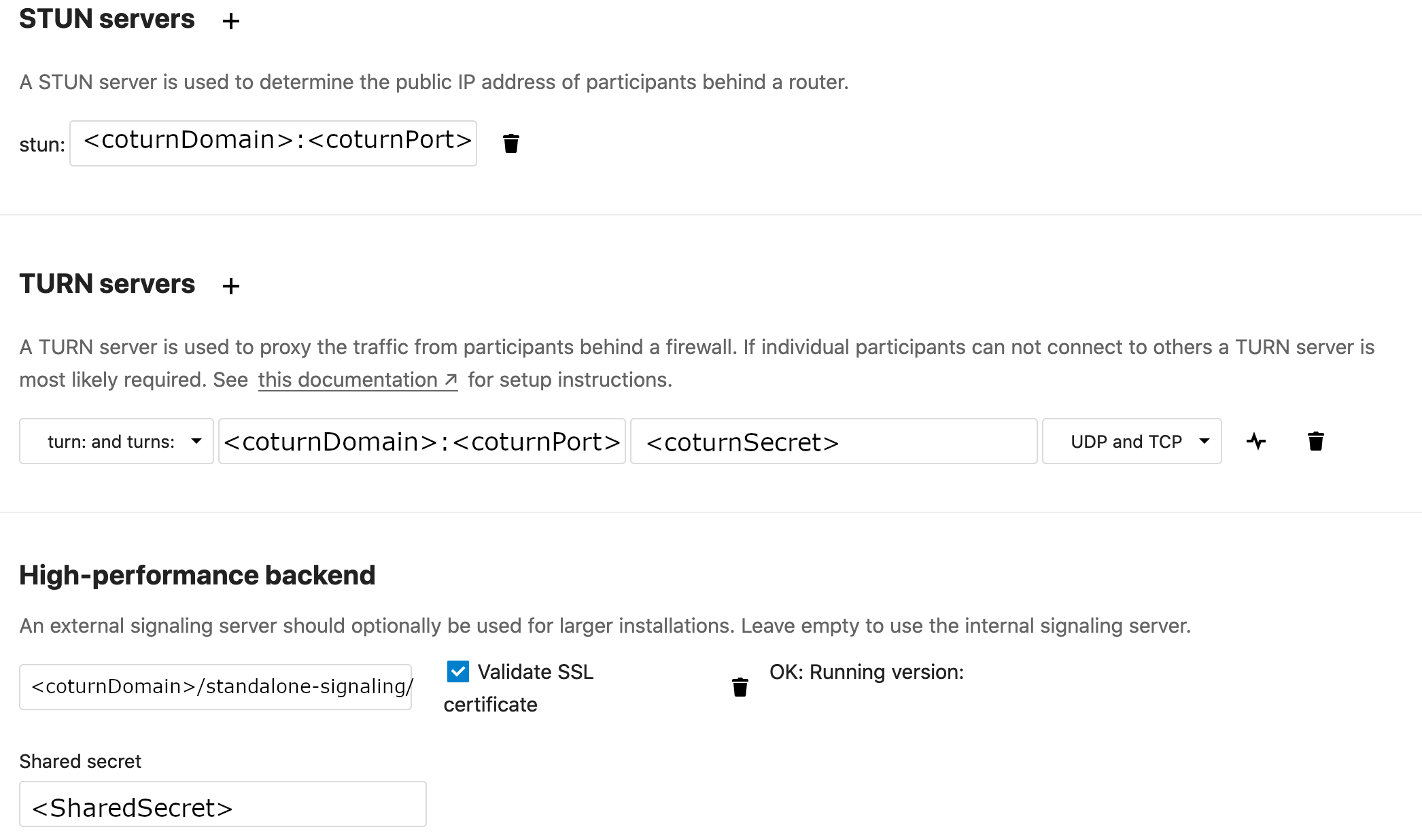
- <hashKey> -
openssl rand -hex 16 - <blockKey> -
openssl rand -hex 16 - <SharedSecret> - used in Nextcloud Talk settings “Shared Secret” and -
openssl rand -hex 16 - <apiKey> - janus.jcfg
turn_rest_api_keyand server.conf → [turn] → apikey -openssl rand -base64 16 - <ipAddress> - IP Address of your server
- <signalingPort> - Listen port for signaling Server
- <NextcloudDomain> - Domain of your Nextcloud instance
- <coturnSecret> - used in server.conf and turnserver.conf -
openssl rand -hex 32 - <coturnDomain> - Domain running coturn including protocol (https!!)
- <coturnPort> - Port used for turn/stun server
NATS Server
Run NATS server using docker
docker run --restart=always --name=NATSSERVER -d -p 4222:4222 -ti --restart=always nats:latest
Configs
- /etc/signaling/server.conf
[http] listen = 127.0.0.1:<signalingPort> [app] debug = true [sessions] hashkey = <hashKey> blockkey = <blockKey> [backend] backends = backend-1 allowall = false # Needs to be false timeout = 10 connectionsperhost = 8 [backend-1] url = <NextcloudDomain> secret = <SharedSecret> [nats] url = nats://localhost:4222 [mcu] type = janus url = ws://0.0.0.0:8188 # Due to some security issue required [turn] apikey = <apiKey> secret = <coturnSecret> servers = turn:<ipAddress>:<coturnPort>?transport=udp,turn:<ipAddress>:<coturnPort>?transport=tcp
- /etc/turnserver.conf
# TURN listener port for UDP and TCP (Default: 3478). # Note: actually, TLS & DTLS sessions can connect to the # "plain" TCP & UDP port(s), too - if allowed by configuration. # listening-port=<coturnPort> # TURN listener port for TLS (Default: 5349). # Note: actually, "plain" TCP & UDP sessions can connect to the TLS & DTLS # port(s), too - if allowed by configuration. The TURN server # "automatically" recognizes the type of traffic. Actually, two listening # endpoints (the "plain" one and the "tls" one) are equivalent in terms of # functionality; but we keep both endpoints to satisfy the RFC 5766 specs. # For secure TCP connections, we currently support SSL version 3 and # TLS version 1.0, 1.1 and 1.2. # For secure UDP connections, we support DTLS version 1. # tls-listening-port=<coturnPort> # Listener IP address of relay server. Multiple listeners can be specified. # If no IP(s) specified in the config file or in the command line options, # then all IPv4 and IPv6 system IPs will be used for listening. # listening-ip=<ipAddress> # Uncomment to use fingerprints in the TURN messages. # By default the fingerprints are off. # fingerprint # Uncomment to use long-term credential mechanism. # By default no credentials mechanism is used (any user allowed). # lt-cred-mech # TURN REST API flag. # Flag that sets a special authorization option that is based upon authentication secret. # This feature can be used with the long-term authentication mechanism, only. # This feature purpose is to support "TURN Server REST API", see # "TURN REST API" link in the project's page # https://github.com/coturn/coturn/ # # This option is used with timestamp: # # usercombo -> "timestamp:userid" # turn user -> usercombo # turn password -> base64(hmac(secret key, usercombo)) # # This allows TURN credentials to be accounted for a specific user id. # If you don't have a suitable id, the timestamp alone can be used. # This option is just turning on secret-based authentication. # The actual value of the secret is defined either by option static-auth-secret, # or can be found in the turn_secret table in the database (see below). # use-auth-secret # 'Static' authentication secret value (a string) for TURN REST API only. # If not set, then the turn server # will try to use the 'dynamic' value in turn_secret table # in user database (if present). The database-stored value can be changed on-the-fly # by a separate program, so this is why that other mode is 'dynamic'. # static-auth-secret=<coturnSecret> # PostgreSQL database connection string in the case that we are using PostgreSQL # as the user database. # This database can be used for long-term credential mechanism # and it can store the secret value for secret-based timed authentication in TURN RESP API. # See http://www.postgresql.org/docs/8.4/static/libpq-connect.html for 8.x PostgreSQL # versions connection string format, see # http://www.postgresql.org/docs/9.2/static/libpq-connect.html#LIBPQ-CONNSTRING # for 9.x and newer connection string formats. # #psql-userdb="host=<host> dbname=<database-name> user=<database-user> password=<database-user-password> connect_timeout=30" # MySQL database connection string in the case that we are using MySQL # as the user database. # This database can be used for long-term credential mechanism # and it can store the secret value for secret-based timed authentication in TURN RESP API. # # Optional connection string parameters for the secure communications (SSL): # ca, capath, cert, key, cipher # (see http://dev.mysql.com/doc/refman/5.1/en/ssl-options.html for the # command options description). # # Use string format as below (space separated parameters, all optional): # #mysql-userdb="host=<host> dbname=<database-name> user=<database-user> password=<database-user-password> port=<port> connect_timeout=<seconds>" # Redis database connection string in the case that we are using Redis # as the user database. # This database can be used for long-term credential mechanism # and it can store the secret value for secret-based timed authentication in TURN RESP API. # Use string format as below (space separated parameters, all optional): # #redis-userdb="ip=<ip-address> dbname=<database-number> password=<database-user-password> port=<port> connect_timeout=<seconds>" # Redis status and statistics database connection string, if used (default - empty, no Redis stats DB used). # This database keeps allocations status information, and it can be also used for publishing # and delivering traffic and allocation event notifications. # The connection string has the same parameters as redis-userdb connection string. # Use string format as below (space separated parameters, all optional): # #redis-statsdb="ip=<ip-address> dbname=<database-number> password=<database-user-password> port=<port> connect_timeout=<seconds>" # The default realm to be used for the users when no explicit # origin/realm relationship was found in the database, or if the TURN # server is not using any database (just the commands-line settings # and the userdb file). Must be used with long-term credentials # mechanism or with TURN REST API. # realm=<coturnDomain> # Total allocation quota. # default value is 0 (no quota). # This option can also be set through the database, for a particular realm. # total-quota=100 # # Maximum server capacity. # Total bytes-per-second bandwidth the TURN server is allowed to allocate # for the sessions, combined (input and output network streams are treated separately). # bps-capacity=0 # Uncomment if extra security is desired, # with nonce value having limited lifetime (600 secs). # By default, the nonce value is unique for a session, # but it has unlimited lifetime. With this option, # the nonce lifetime is limited to 600 seconds, after that # the client will get 438 error and will have to re-authenticate itself. # stale-nonce # Certificate file. # Use an absolute path or path relative to the # configuration file. # cert=/etc/letsencrypt/path/cert.pem # Private key file. # Use an absolute path or path relative to the # configuration file. # Use PEM file format. # pkey=/etc/letsencrypt/path/privkey.pem # Allowed OpenSSL cipher list for TLS/DTLS connections. # Default value is "DEFAULT". # #cipher-list="DEFAULT" cipher-list="ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AES:RSA+3DES:!ADH:!AECDH:!MD5" # Flag that can be used to disallow peers on the loopback addresses (127.x.x.x and ::1). # This is an extra security measure. # no-loopback-peers # Flag that can be used to disallow peers on well-known broadcast addresses (224.0.0.0 and above, and FFXX:*). # This is an extra security measure. # no-multicast-peers
- /etc/janus/janus.jcfg
nat: { stun_server = "<coturnDomain>" stun_port = <coturnPort> full_trickle = true turn_server = "<coturnDomain>" turn_port = <coturnPort> turn_type = "udp" turn_rest_api_key = "<apiKey>" }
Extend <coturnDomain> vhost file
- apache.vhost
<VirtualHost *:443> # ... # Enable proxying Websocket requests to the standalone signaling server. ProxyPass "/standalone-signaling/" "ws://127.0.0.1:<signalingPort>/" RewriteEngine On # Websocket connections from the clients. RewriteRule ^/standalone-signaling/spreed$ - [L] # Backend connections from Nextcloud. RewriteRule ^/standalone-signaling/api/(.*) http://127.0.0.1:<signalingPort>/api/$1 [L,P] # ... </VirtualHost>
Nextcloud GUI configuration
nextcloud-talk-high-performance-backend.1618957227.txt.gz · Last modified: by admin